Configure MTA-STS
MTA Strict Transport Security (MTA-STS ↗) was introduced by email service providers including Microsoft, Google and Yahoo as a solution to protect against downgrade and man-in-the-middle attacks in SMTP sessions, as well as solving the lack of security-first communication standards in email.
Suppose that example.com is your domain and uses Email Routing. Here is how you can enable MTA-STS for it.
- Log in to the Cloudflare dashboard ↗ and select your account and domain.
- Go to DNS > Records and create a new CNAME record with the name
_mta-ststhat points to Cloudflare’s record_mta-sts.mx.cloudflare.net. Make sure to disable the proxy mode.
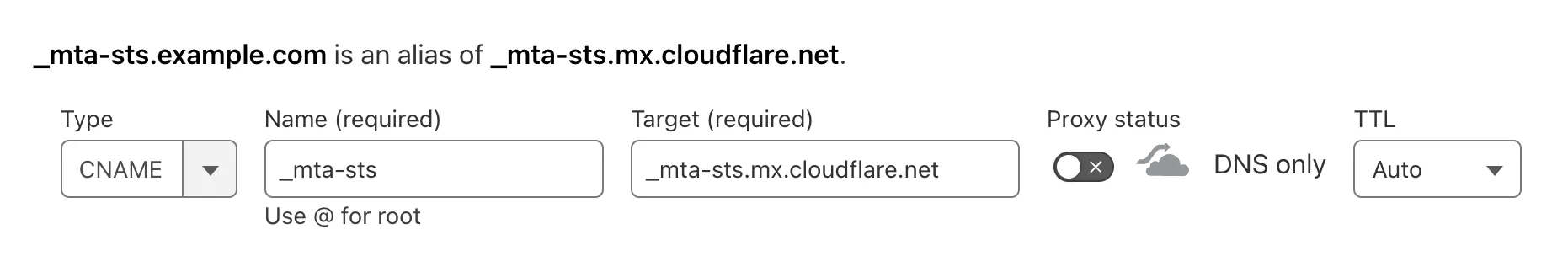
- Confirm that the record was created:
dig txt _mta-sts.example.com_mta-sts.example.com. 300 IN CNAME _mta-sts.mx.cloudflare.net._mta-sts.mx.cloudflare.net. 300 IN TXT "v=STSv1; id=20230615T153000;"This tells the other end client that is trying to connect to us that we support MTA-STS.
Next you need an HTTPS endpoint at mta-sts.example.com to serve your policy file. This file defines the mail servers in the domain that use MTA-STS. The reason why HTTPS is used here instead of DNS is because not everyone uses DNSSEC yet, so we want to avoid another MITM attack vector.
To do this you need to deploy a Worker that allows email clients to pull Cloudflare’s Email Routing policy file using the “well-known” URI convention.
- Go to your Account > Workers & Pages and press Create Application. Pick the “MTA-STS” template from the list.
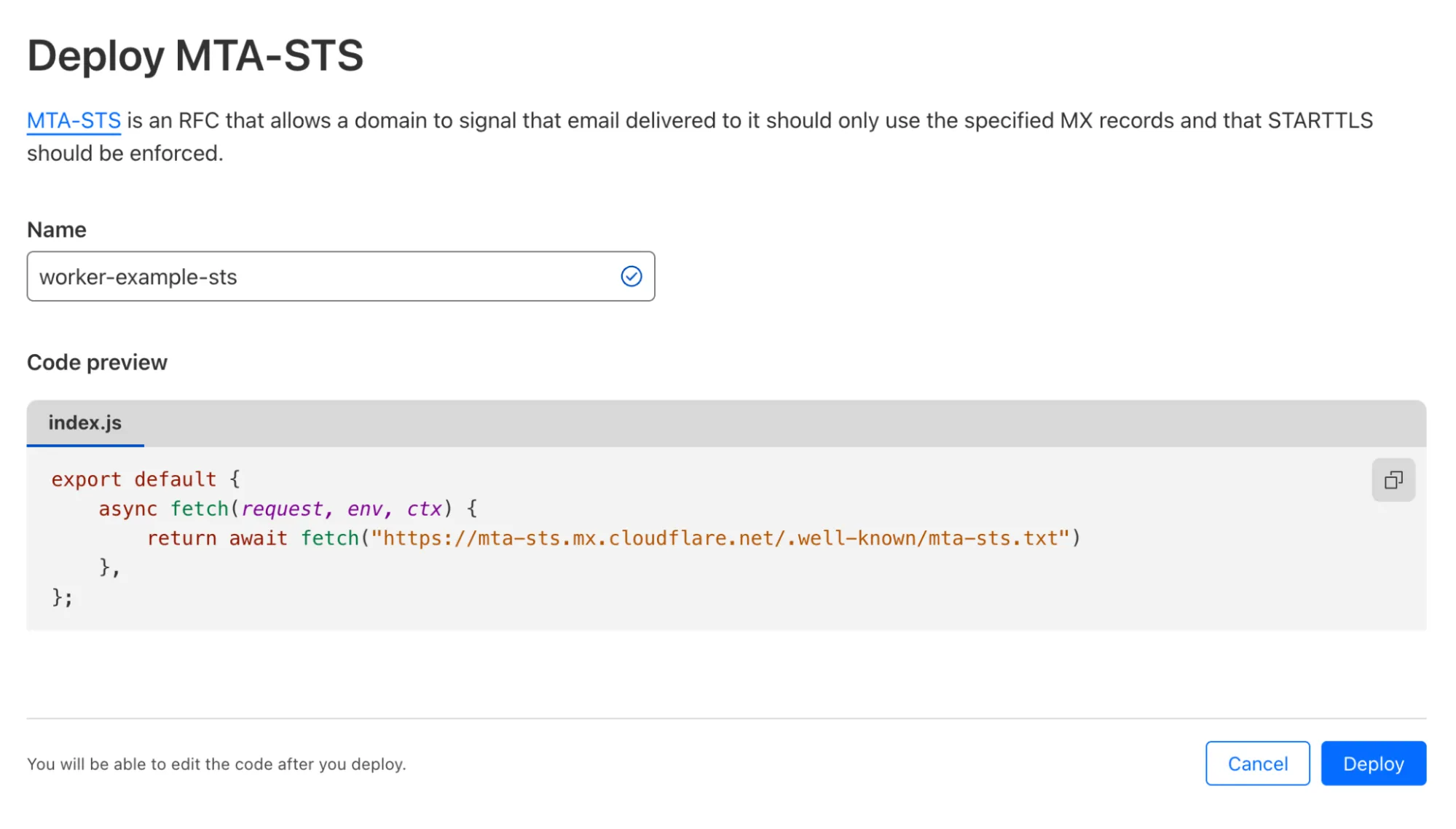
- This Worker proxies
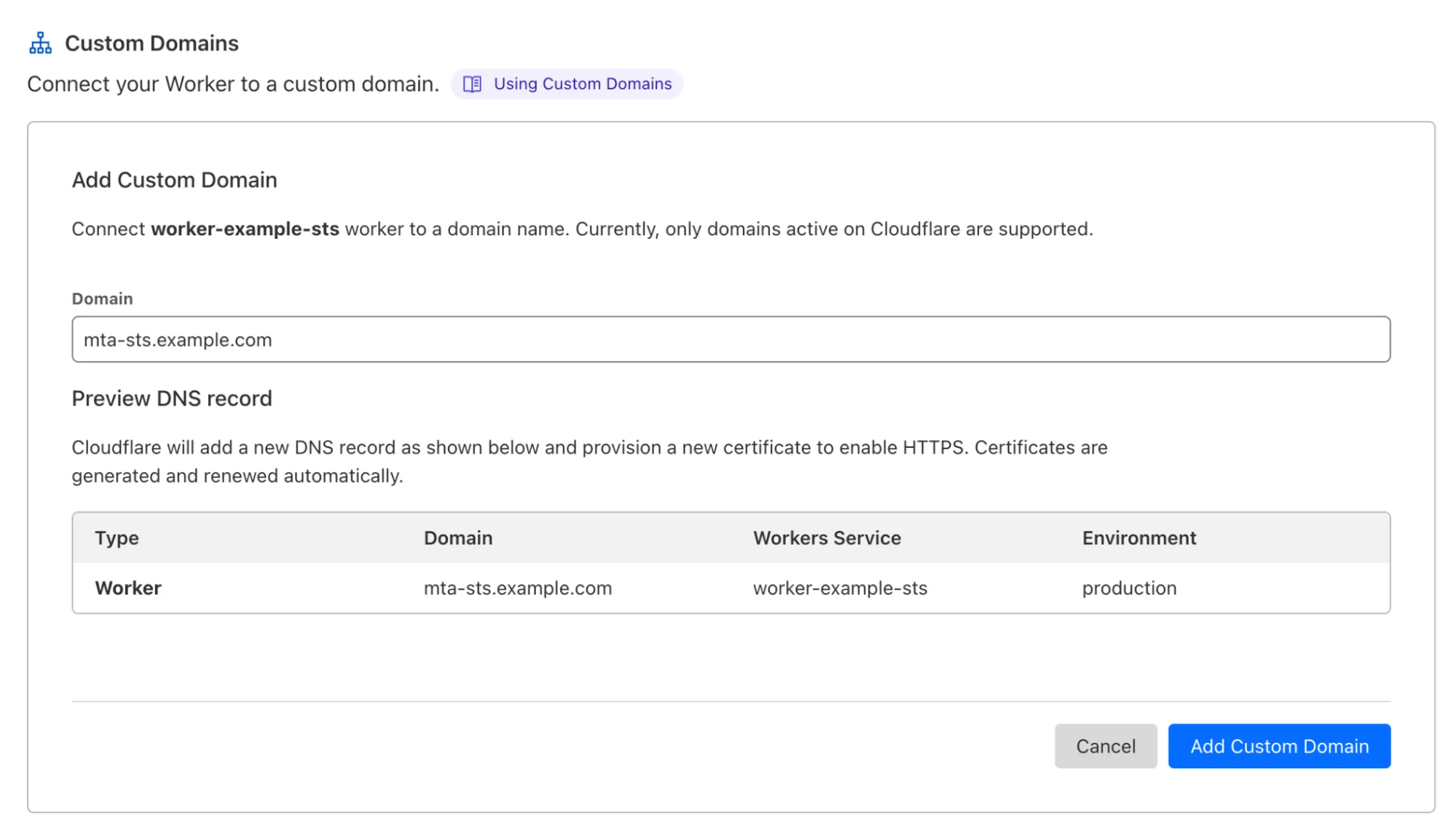
https://mta-sts.mx.cloudflare.net/.well-known/mta-sts.txtto your own domain. After deploying it, go to the Worker configuration, then Triggers > Custom Domains and Add Custom Domain. Type the subdomainmta-sts.example.com.
You can then confirm that your policy file is working with the following:
curl https://mta-sts.example.com/.well-known/mta-sts.txtversion: STSv1mode: enforcemx: *.mx.cloudflare.netmax_age: 86400This says that you domain example.com enforces MTA-STS. Capable email clients will only deliver email to this domain over a secure connection to the specified MX servers. If no secure connection can be established the email will not be delivered.
Email Routing also supports MTA-STS upstream, which greatly improves security when forwarding your Emails to service providers like Gmail, Microsoft, and others.
While enabling MTA-STS involves a few steps today, we aim to simplify things for you and automatically configure MTA-STS for your domains from the Email Routing dashboard as a future improvement.